| Authentication Process Combination | MFA? | Why or Why not? |
|---|
| Password + PIN | No | Something you know + Something you know → Same Factors |
| Finger Print + Draw a Pattern | Yes | Something you Are + Something you Do → Different Factors |
| Facial Recognition + Smart Card | Yes | Something you Are + Something you Have → Different Factors |
| GPS Location + User Credentials | Yes | Somewhere you Are + Something you Know → Different Factors |
| Voice Print + Retinal Scan | No | Something you Are + Something you Are → Same Factors |
| Iris Scan + Finger Print + PIN | Yes | 2 x Something you Are + Something you Know → Different factor on the last process than on the first two processes |
| Voice Recognition + Facial Recognition + Finger Print | No | 3 x Something you Are →Same Factors |
| User Credentials + Finger Print + Credit Card | Yes | Something you Know + Somthing you Are + Something you Have → Different Factors on all three processes |
| Protocol | TCP or UDP | Port # | Description |
|---|
| Password Authentication Protocol (PAP) | TCP | 3666 | A simple authentication protocol in which the user credentials are sent in plain text (unencrypted) - Insecure
|
| Challenge Handshake Authentication Protocol (CHAP) | NA | runs at Data Link Layer | A protocol that sends usernames in plain text, but uses Message Digest version 5 (MD5) encryption to send passwords to an authenticator via Point-to-Point Protocol (PPP) to provide on-demand authentication with on-going data transmission - Secure
|
| MicroSoft - CHAP (MS-CHAP) | NA | runs at Data Link Layer | Microsoft's version of CHAP which came with version 1 and version 2 - both versions are insecure.
However, MS-CHAP can be used with the following protocols to enhance security:
|
| Extensible Authentication Protocol (EAP) | NA | runs at Data Link Layer | An authentication framework which supports multiple authentication
methods |
| Remote Authentication Dial In User Service (RADIUS) | TCP and UDP | 1812 - Athentication Process | An access server authentication and accounting protocol that manages a single "database" of users, which allows for authentication (verifying user name and password) as well as configuration information detailing the type of service to deliver to the user (for example, SLIP, PPP, telnet, rlogin). RADIUS uses UDP. |
| 1645 - Authentication Request |
| 1813 - Accounting Process |
| 1646 - Accounting Request |
| Terminal Access Controller Access-Control System (TACACS) | TCP | 49 | A security application that provides centralized validation of users attempting to gain access to a router or network access server
|
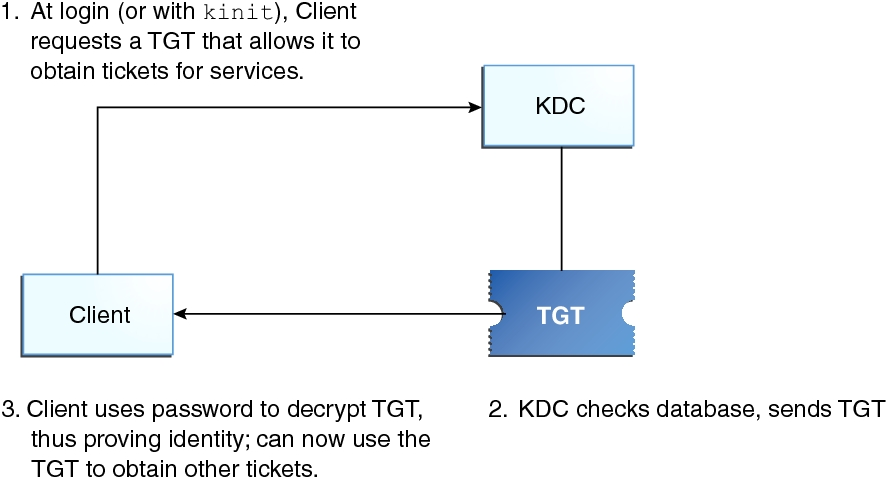
| Kerberos | TCP and UDP | 88 | Designed to provide strong authentication for client/server applications by using a symmetric secret-key cryptography which is Ticket-based (see below)
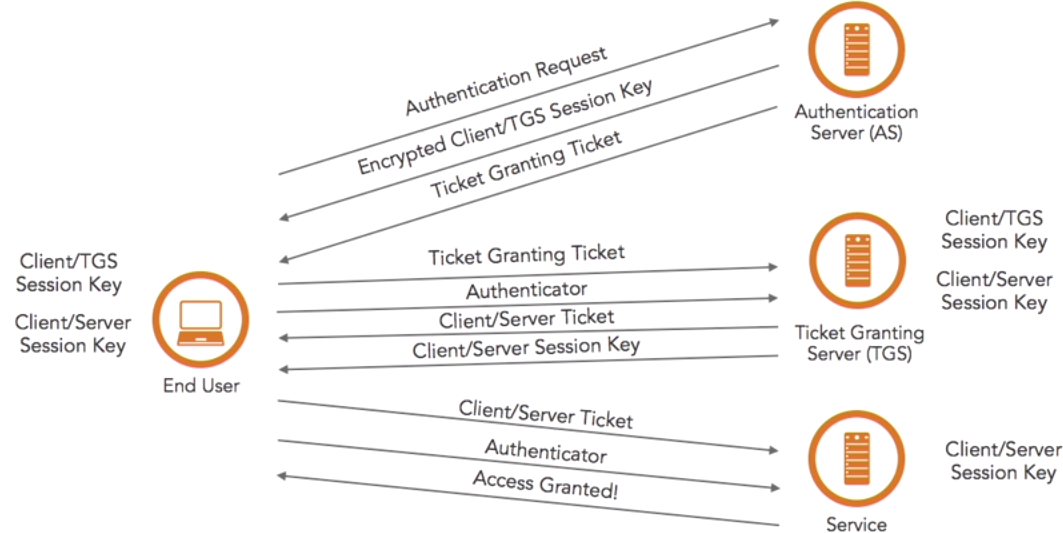
Please review the Kerberos authentication process for more information. |
| Light weight Directory Protocol (LDAP) | TCP and UDP | 389 (unencrypted) | Insecure protocol for authentication that uses BIND to authenticate users, except the connection is unencrypted |
| 636 (encrypted) | Secure protocol for authentication that uses BIND to authenticate users |
| New Technology Login Management (NTLM) | UDP | 137 - NetBIOS Name | Not secure (Microsoft recommends disabling) - This was widely used on older Windows systems before Kerberos and LDAP became widely available - Uses the Security Account Manager (SAM) to validate users |
| UDP | 138 - NetBIOS Netlogon and Browsing |
| TCP | 139 - NetBIOS Session |
*