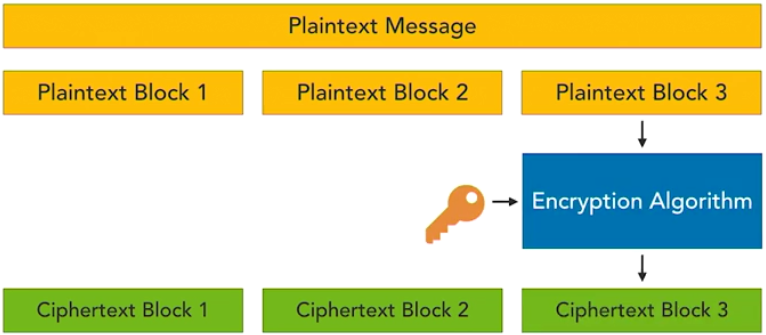
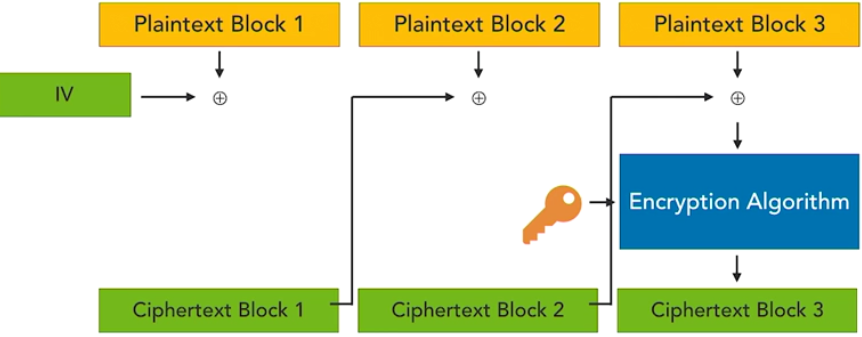
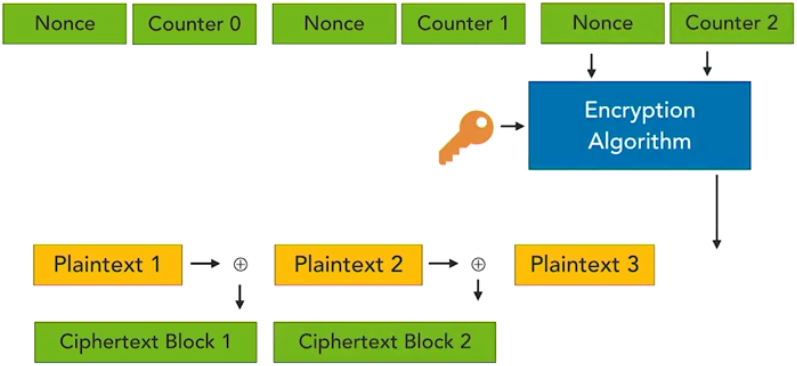
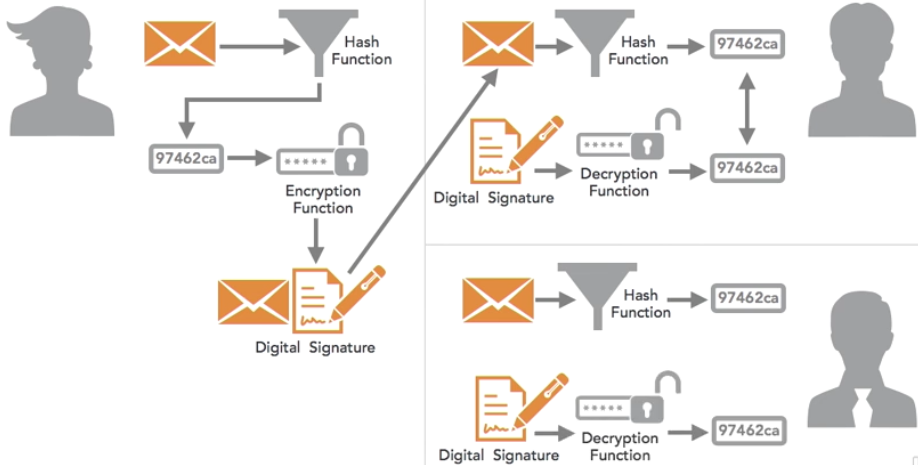
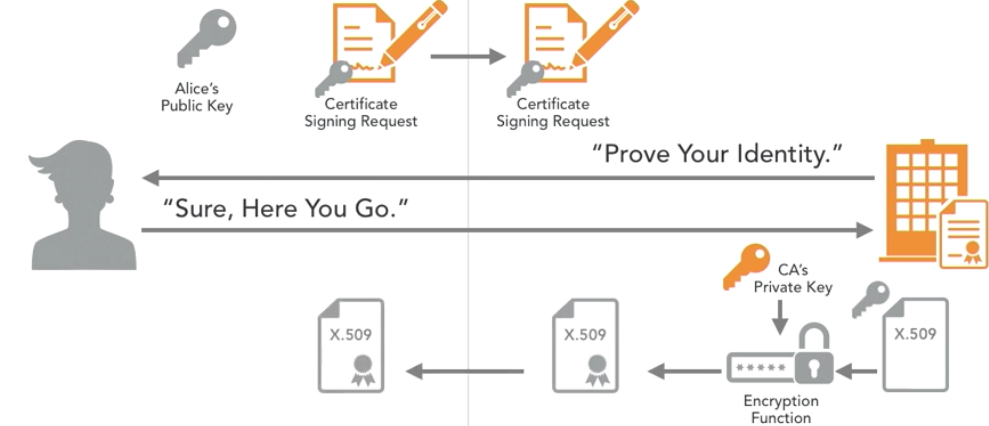
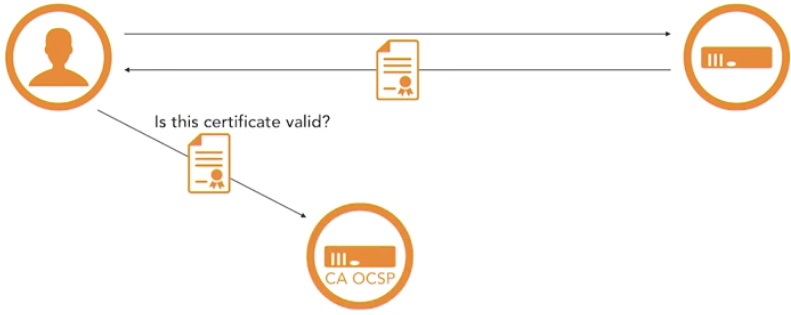
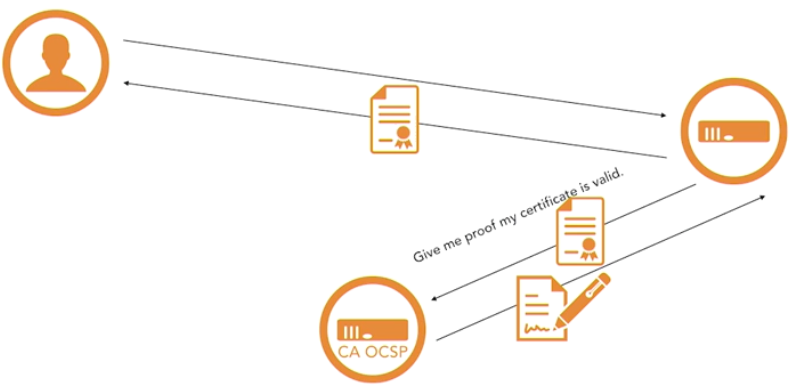
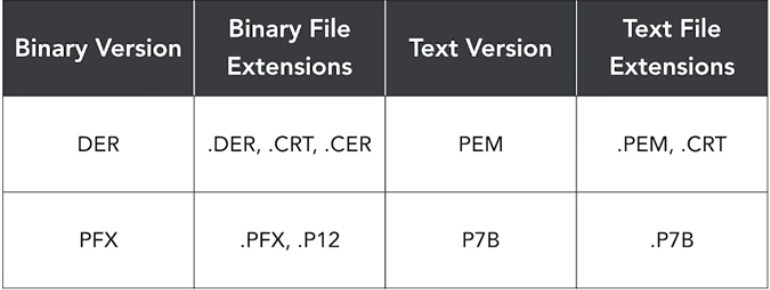
Here are some things you need to know for the Security+ examination.
| Algorithm | Secure? | Symmetry | Comments |
|---|
| Rijndael algorithm or Advanced Encryption Standard (AES) | Yes | Symmetric | An encryption algorithm that Vincent Rijmen and Joan Daemen developed in January 2002 that is similar to the Data Encryption Standard, but uses 128-bit, 160-bit, 192-bit, 224-bit or 256-bit cipher blocks and is used in Wi-fi Protected Access version 2 (WPA2) communications |
| Data Encryption Standard (DES) | No | Symmetric | An algorithm developed by IBM in 1977 that uses the Horst Feistel function for 16 rounds of encryption, using 64-bit cipher blocks with a 56-bit key. This was based on the Lucifer algorithm. This was considered a secure encryption standard until December 2001. |
| Tripple DES (3DES) | Yes* | Symmetric | This a modified version of DES encryption algorithm algorithm that Walter Tuchman and his associates at IBM developed in 1999 that uses 3 rounds of DES (i.e. 64-bit cipher blocks) to encrypt plain text, using 3 different keys, using one of the following 3 options:
- K1 ≠ K2 ≠ K3 ≠ K1 - Effectively 168-bit encryption (best option)
- K1 ≠ K2 & K1 = K3 ∴ K2 ≠ K3 - Effectively 112-bit encryption (subject to the meet-in-the-middle attack ∴ no more secure than regular DES)
- K1 = K2 = K3 - Effectively 56-bit encryption (just as insecure as regular DES)
|
| Lucifer algorithm | No | Symmetric | This was an encryption algorithm that Horst Feistel originally proposed on Tuesday, 01 May 1973, which used a 112-bit encryption key which became the basis for DES. |
| Blowfish (free) | No | Symmetric | This was developed by Bruce Scheier in 1993 as an alternate to DES that has the following characteristics:
- Uses a 64-bit block and variable key length from 32 bits to 448 bits
- Is free (no license required)
- Uses a Fiestel network
- Optimized for performance on 32-bit processors
- Combines substitution and transposition
|
| Twofish (Free) | Yes | Symmetric | Developed by Bruce Scheier in 1998 as a replacement to DES which has the following characteristics:
- Uses a 128-bit block size
- Key sizes of 128 bits, 192 bits or 256 bits
- Uses a Fiestel network
- Combines substitution and transposition
This was 1 of 5 finalists for the Advanced Encryption Security competition, but lost to the Rijndael algorithm which became the selected algorithm. |
| Ron's Cipher version 4 (RC4) | No | Symmetric | This is an encryption algorithm that Ron Rivest develped in 1987 as a trade secret, but was leaked to the public in 1994. This was one of the forerunners of RSA. This uses the XOR (⊕) function with a pseudorandom keystream on each character (byte) for encryption and decryption. The key length is variable from 40 bits to 2,048 bits. This was used with the following standards: While there are no known instances of anyone breaking RC4, some experts found vulnerabilities in RC4 in 2015 ∴ RC4 is considered insecure. |
| RSA (variable length) | Yes | Asymmetric | Developed by Ron Rivest, Adi Shamir and Leonard M. Adleman in the 1970s that creates key pairs (public & private), using very large prime numbers and uses variable length keys from 1,024 bits and 4,096 bits. Therefore, RSA requires more computing power |
| Quantum Cryptography | Yes | Symmetric and Asymmetric | This employs quantum computing which is mostly theoretical that draws it strength from the weirdness or reality at small scales (≤ 100 μm) which results in Quantum Key Distribution (QKD) which uses a Quantum key that encodes and sends the information needed to decrypt a message in the fuzzy properties of particles, typically light particles. Therefore, it is not as susceptable as Elliptic Curve Cryptography (ECC) or RSA. |
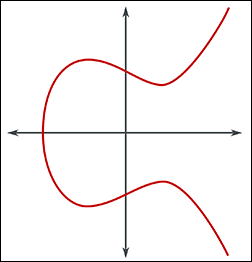
| Elliptic Curve Cryptography (ECC) | Yes | Symmetric and Asymmetric | Uses the mathematical properties of elliptic curves to produce public key cryptographic systems. The following formula is used to draw the curve:
y2 + axy + by = x3 + cx2 + dx + e � where a, b, c, d, and e, are real numbers.
 |
| Elliptic Curve Diffie-Hellman (ECDH) | Yes | Symmetric and Asymmetric | ECDH works the same way as Diffie-Hellman (DH) as shown below, except that it adds the functionality of ECC for more secure communications. A group number of 14 (2,048-bit) or greater is considered secure. Higher number group numbers combines the ECC algorithm with the Diffie-Hellman algorithm to create a more secure algorithm. The higher the group number, the higher the security. |
| Diffie-Hellman (DH) | Yes | Symmetric and Asymmetric | Developed in 1976 by Ralph C. Merkle, Bailey Whitfield Diffie and Martin Hellman as the first practical way of sending private messages by using a shared secret over an unsecured communication channel. Asymmetric encryption is used as a technique in key exchange mechanism to share secret key, but does not use prime factorization (see below for concept). After the key is shared between sender and receiver, the communication will take place using symmetric encryption. The shared secret key will be used to encrypt the communication.
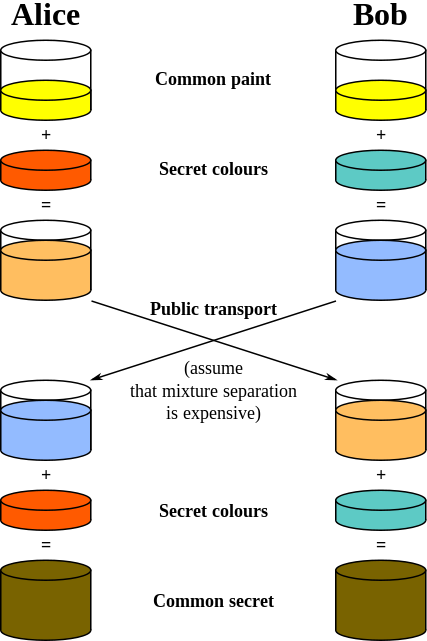
The shared secret is the symmetric key that is used to encrypt the message. |
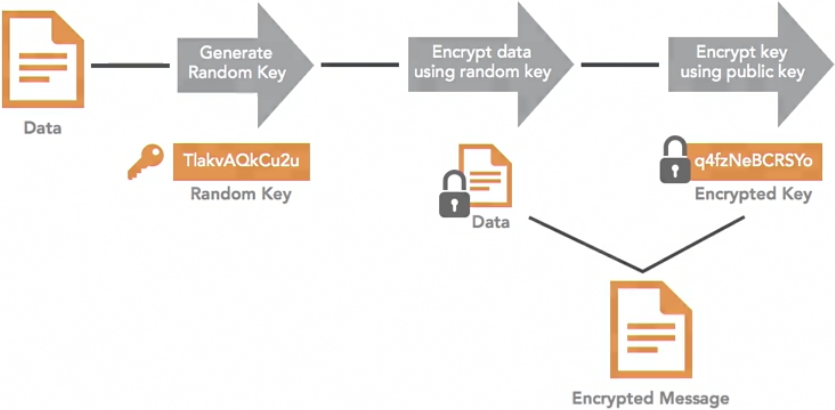
| Pretty Good Privacy (PGP)+ | No | Symmetric and Asymmetric | Developed by Phil Zimmerman in 1991 that goes through the following process to encrypt the message:
- Generates a random key
- Encrypts data, using a random key
- Encrypts the key, using a public key
- Produces the encrypted message with the encrypted data and encrypted public key.
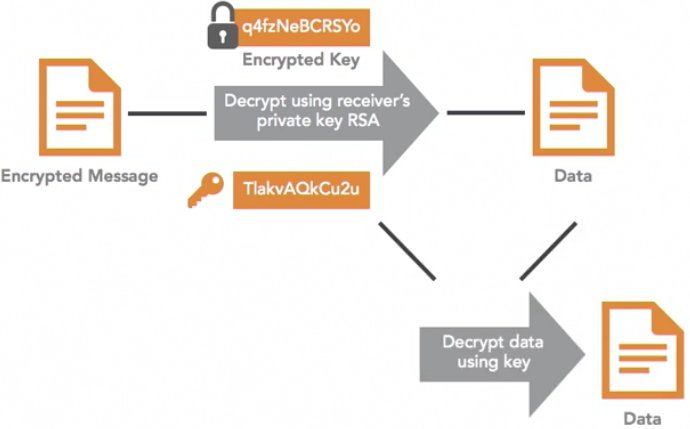
and goes through the following process to decrypt the message:
- Uses the private key to decrypt the original key and produce the encrypted data
- Uses the original key to decrypt the data. This relies on other encryption algorithms (e.g. RSA) to encrypt and decrypt the symmetric key the original message.
There are commercial versions of PGP which are patented! There may be some versions that are secure, but for the most part, including the original version, are insecure. |
GnuPG (GPG)+
also known as OpenGPG+ | No | Symmetric and Asymmetric | This works the same way that PGP works and relies on other encryption algorithms (e.g. RSA) to encrypt and decrypt the symmetric key the original message, except that it is Open Source and Free (no patent). |
*
| Hashing Algorithm | Secure? | Description |
|---|
| Message Digest version 5 (MD5) | No | The 5th edition of the original Message Digest algorithm that Ron Rivest in 1991 which is 128-bit function.
|
| Secure Hash Algorithm (SHA) | Version 1
No
Version 2
Yes
Version 3
Yes | Is like a signature for a data set. For example,
- SHA-256 for "I'm going to lunch!"
"1da8a8c7d34de4f64789fce41532d701e7329c6f8a936d50c84f45a7b631b657" and
- SHA-256 for "I am going to lunch!" is "fb9c0f97bb45abc85b0869ff84d88720d88d9063c7e62e525838eb5adc672f74"
Version 3 has the following properties:
- Designed as a replacement for version 2
- Uses a completely different hash generation approach than version 2
- Produces hashes of user-selected fixed length
|
| RACE Integrity Primitives Evaluation Message Digest (RIPEMD) | Yes* | Developed by Hans Dobbertin, Antoon Bosselaers and Bart Preneel in 1992 to work well with 32-bit processors.Types of RIPEMD:
- RIPEMD-128
- RIPEMD-160
- RIPEMD-256
- RIPEMD-320
|
| Hash-based Message Authentication Code (HMAC) | Yes | used with asymmetric encryption algorithms |
* if using 160+ bit